
Stealing Data from Computers Using Heat
Stealing Data from Computers Using Heat
March 26, 2015
Wired — Air-gapped systems, which are isolated from the Internet and are not connected to other systems connected to the Internet, are used in situations that demand high security because they make siphoning data from them difficult.
Now BGU cyber security researchers have found a way to retrieve data from an air-gapped computer using only heat emissions and a computer’s built-in thermal sensors. This method could be used by attackers to surreptitiously siphon passwords or security keys from a protected system and transmit the data to an Internet-connected system in close proximity that the attackers control.
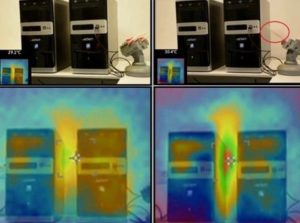
Two air-gapped PCs positioned in the parallel layout. Using BGU’s BitWhisper, the left computer transmits a command to the right computer using heat.
They could then use the Internet-connected system to send malicious commands to the air-gapped system using the same heat and sensor technique.
Here’s how it works.
Computers produce varying levels of heat depending on how much processing they’re doing. In addition to the CPU, the graphics-processing unit and other motherboard components produce significant heat as well. A system that is simultaneously streaming video, downloading files and surfing the Internet consumes a lot of power and generate heat.
To monitor the temperature, computers have a number of built-in thermal sensors to detect heat fluctuations and trigger an internal fan to cool the system off when necessary or even shut it down to avoid damage.
The attack, which the researchers dubbed BitWhisper, uses these sensors to send commands to an air-gapped system or siphon data from it. The technique works a bit like Morse code, with the transmitting system using controlled increases of heat to communicate with the receiving system, which uses its built-in thermal sensors to then detect the temperature changes and translate them into a binary “1” or “0.”
The method was developed by Mordechai Guri, Ph.D. in a project overseen by his adviser, Prof. Yuval Elovici, director of the BGU Cyber Security Research Center.
“The research represents just a first step,” says Prof. Dudu Mimran, the Center’s chief technology officer, who says they plan to present their findings at an upcoming security conference in Tel Aviv and release a paper describing their work.
With additional research, they say they may be able to increase the distance between the two communicating computers and the speed of data transfer between them.
In a demonstration, the researchers used one computer tower to initiate a command to an adjacent computer tower representing an air-gapped system.
However, future research might involve using the so-called Internet of things as an attack vector — an Internet-connected heating and air conditioning system or a fax machine that’s remotely accessible and can be compromised to emit controlled fluctuations in temperature.



