
How a Business Card Can Turn Your Phone Into a Spy
How a Business Card Can Turn Your Phone Into a Spy
June 24, 2016
Forbes — Hoarding business cards seems to be a requisite habit of every modern business person. But what if hidden inside the next one you receive was a little spy device, one that could use your phone to transmit information to a snoop’s computer via its gyroscope?
That’s what researchers Benyamin Farshteindiker, Nir Hasidim, Asaf Grosz, and Yossi Oren of BGU’s Faculty of Engineering Sciences have proposed in a recently released paper.
In a conversation with Forbes, Oren revealed that for just three dollars he could install a small device in a business card or even a sticker that would use an audio signal to force a phone or tablet gyroscope to vibrate at its resonant frequency. This frequency would be registered by code running on the target’s phone — most likely within an innocent-looking web page — that queries the gyroscope as quickly as possible, uploading its reading to a server.
In their own proof-of-concept, the researchers used an iPhone 5S, a Samsung Galaxy S5 and a Microsoft Surface Pro 3 tablet. As they received the audio signal from the implant device, the state of the gyroscope was collected and sent to an external server by JavaScript code running on a web page.
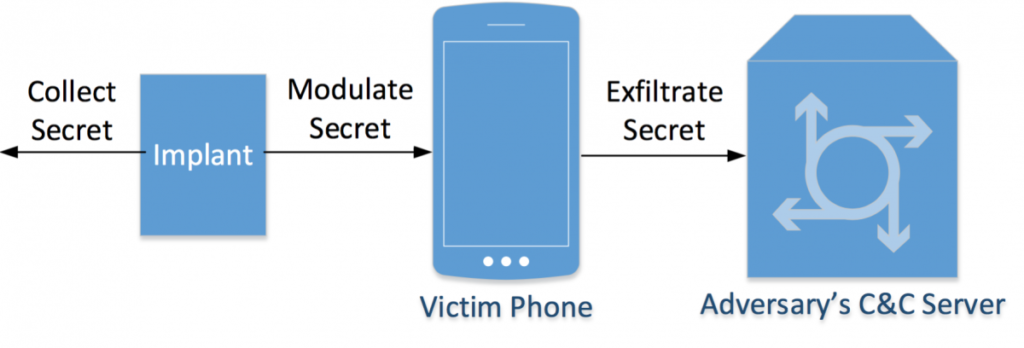
A diagram showing the basic methodology to turn a phone’s gyroscope into a spy tool for transmitting data.
The researchers believe the attack method would allow an intelligence agency “to monitor many implants at the same time at a low cost, with no risk of exposure to their field agents.”
What makes the gyroscope such an attractive feature for exploitation is that unlike microphones or cameras, the rotation sensor does not require any special permissions to be used by external parties.
There is potential for the little implant to be used as part of a two-factor authentication mechanism, adding security. However, there is potential for malicious use.
“This new attack vector changes the economics of state-sponsored attacks, and can induce malicious intelligence agencies to activate all of the implants they distribute, not only a selected few, thus drastically raising the amount of people targeted by hardware-based spying methods,” the researchers say.



